Description:
Learn the way with the help of which cyber incidents at the global level influenced the approaches and directions of the cybersecurity sphere’s development. Get to know when such events occurred, what their results were, and what they shaped the modern cybersecurity industry.
Introduction:
Cyber threats have taken great tolls while at the same time triggering change processes. Since the inception of the world wide web until the current always connected environment dominated by smart devices, every instance of malware was educational. By 2021, worldwide cybercriminal loss and damage are estimated to reach $10.5 trillion per year? This figure alone is why learning about the development of cybersecurity is so important. In the following article, let’s reflect on how global malware incidents responded not only to weaknesses but also to pioneers in the sphere of cybersecurity.
1. The Early Days of Malware: Setting the Stage for Cybersecurity
• misuse of the names Trojan horses and viruses, as well as the emergence of the first malware forms, worms and viruses.
• Specific events that pointed to the phenomena in the early 1980s and the early 1990s, for example the Morris Worm.
• How these incidents reflected the problem of the lack of systematic approaches to cyber security.
• Notable incidents from the 1980s and 1990s, such as the Morris Worm.
• How these incidents revealed the need for systematic cybersecurity.
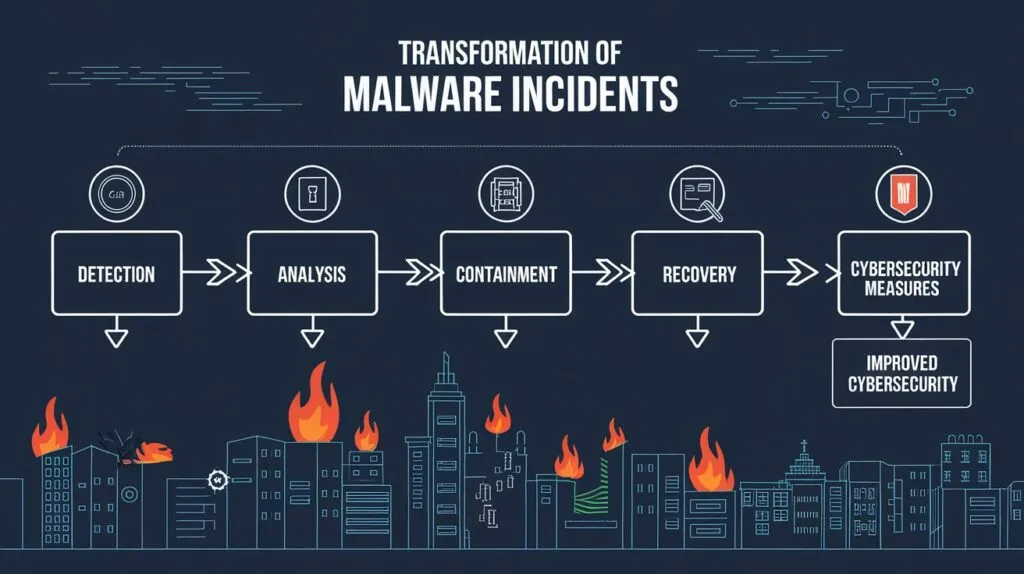
2. Landmark Malware Incidents That Changed the Game
- ILOVEYOU (2000): The first worldwide email virus.
- Stuxnet (2010): The first malware targeting critical infrastructure.
- WannaCry (2017): A ransomware attack with massive global impact.
- Overview of the lessons learned from these events.
3. The Rise of Sophisticated Malware in a Hyper-Connected World
• One of the more strategic threat actors: Advanced Persistent Threats (APTs) and state sponsored actors.
• Moving to the age of Artificial Intelligence malware and polymorphic threats.
• The article’s main focus is on the connections between malware and IoT devices.
• The shift to AI-driven malware and polymorphic threats.
• The growing contribution of IoT devices to the spread of malware.
4. How Global Incidents Have Driven Cybersecurity Innovations
• The move from the simple antivirus to the complex cybersecurity solution software.
• Increase in cloud workload protection platforms.
• Building of international frameworks as well as cooperation in the field of cybersecurity. Ions.
• The rise of endpoint detection and response (EDR) tools.
• Development of international cybersecurity frameworks and collaboration.
5. Case Studies: Real-World Impact of Malware Attacks
• A case of a significant tampering of a prominent organization’s financial records by a virus.
• Cost of ransomware attacks on healthcare and public organizations.
• Business and government actions and outcomes in depth..
• Impact of ransomware on healthcare and public infrastructure.
• How businesses and governments responded and recovered.
6. Preparing for the Future: Cybersecurity Lessons from Malware History
• The need to focus on threat intelligence and to taking preemptive measures.
• How cyber-security is responding to the rise of AI/malware combinations.
• Measures that companies can take in order to prepare for future risk. unity is adapting to AI-powered malware.
• Steps organizations can take to build resilience against future threats.
Conclusion:
Cyber attacks and malware cases are not only evils but also alarm bells. Both have has served as a catalyst and forced the cybersecurity industry to adapt and improve itself. Criminals have not stood still and hence more changes are inevitable. Are you ready to read the next chapter in protecting your digital world? Don’t forget the past, don’t lose the present and don’t neglect the future.
Cybersecurity Best Practices: Protecting Your Digital World
Today, cybersecurity is no longer a luxury, it’s an absolute necessity in the world we live in. Cyber threats are developing rapidly and they are affecting where individuals and organisations are concerned. The best practice must be adopted in order to remain secure. Learn how to protect yourself from harm to your digital life.
1. Use Strong, Unique Passwords
Your first line of defense is having a robust password. Don’t repeat same password for two accounts, never ever use all or part of the password in the dictionary usage. The best thing is, let the password manager generate and store them securely for you.
2. And enable Multi-Factor Authentication (MFA)
MFA adds one more level of security to your account – requiring you to provide a second form of verification, like a text code, or biometric scan of some sort to verify you are who you are. It cuts down to a great extent the risk of intrusion by unauthorized persons..
3. Keep Software Updated
Hackers love to attack outdated software. Keep your operating system, applicable apps, and antivirus software up-to-date to get future patch vulnerabilities and be saved from different threats.
4. Be Wary of Phishing Attempts
Many cyber criminals use very deceptive emails and web sites to steal your sensitive information. Make sure you always double check the sender’s address, do not click on unknown links, and check to see if a web site is a checked and real one before entering your credentials.
5. Secure Your Network
Make your router firmware up-to-date and, of course, use a solid Wi-Fi password. In particular, take a look at using a Virtual Private Network (VPN) to access the Internet in a secure way.
6. Back Up Your Data Regularly
Losing your critical data to ransomware attacks is no longer a hypothetical situation. Backups are made to secure cloud storage, or external drives so that your information can be recovered should you lose everything.
7. Get Educated Yourself and Your Team
Cybersecurity is all about knowledge is power. Keep informed of the newest threats and train employees on how to respond to those risks if they see them.
8. Limit Permissions and Access
Ensure that only access to the sensitive information is restricted according to roles and then adopt the principle of least privilege. It lessens the blow of potential breaches, too.
Conclusion
Cybersecurity is a shared responsibility. By implementing these best practices, you can reduce vulnerabilities and safeguard your data against evolving threats. Take action today—your digital safety depends on it!
Financial Sector Cyber Threats: Protecting Assets in a Digital Era
Cyber criminals have the financial sector in their sights as a prime target. Banks, investment firms and payment systems are dealing with relentless cyber threats with vast amounts of sensitive data and monetary transactions. If you understand these threats, you can fortify defenses.

1. Phishing and Social Engineering Attacking Points
Phishing is still top threat, where attackers will use their fake identity impersonate a trusted entity and steal credentials or engage in fraudulent transactions. Social engineering is the use of human vulnerabilities in order to deceive employees and customers into disclosing sensitive information.
2. Ransomware Attacks
One of the most devastating threats has evolved from Ransomware. Criminals are encrypting critical systems and then demanding heavy ransoms as they disrupt operations and risk exposing the data. It is precisely because of the need for real time access to data for the financial sector that it is extremely vulnerable.
3. Insider Threats
Not all threats are coming from actors external to your organisation. They are usual cause for data breaches or financial loss; malicious or negligent insiders like employees or contractors can cause security to be compromised inadvertently or intentionally.
4. Advanced Persistent Threats (APTs)
that are designed to carry out targeted personal or organizational service disruptions within a corporate network, these tools are associated by the company with high audio and video quality.
APT is being used by the nation state actors and sophisticated criminal groups to extort networks in finance. The objective of these long term campaigns is to extract this sensitive data or to disrupt critical infrastructure.
5. Supply Chain Attacks
Attackers often enter through third party vendors. Vendor security is growing concern because compromising a supplier’s system can give access to financial institutions’ networks.

6. DDoS Attacks
DDoS attacks send massive amounts of traffic to financial systems which disrupts business and online banking services and payment systems. These attacks can steal reputation and consumer trust while creating massive operational downtime.How Financial Institutions Can Mitigate Risks
• Implement Robust Authentication: Protect accounts and transactions with multi factor authentication.
• Regularly Update Systems: Fix the patches for the software, systems and devices as soon as possible.
• Employee Training: Teach your staff what phishing, social engineering, and other common attack vectors are.
• Monitor and Respond: Use of advanced threat detection tools for identifying and reacting to suspicious activities.
• Secure Third-Party Access: The vet vendors are careful and do confirm with the security protocols.
Conclusion
Scale and sophistication of cyber threats to the financial sector are expanding and proactive measures can be taken to reduce risks. Finances are digital, and the world is digital; so much so that those of us who rely on them to protect our investment and assets need to stay vigilant and invest in the types of solutions that will protect our data and our trustworthiness.


