Description:
Learn how to identify and fix risk or control gaps in cybersecurity. This comprehensive guide for 2025 provides strategies, best practices, and actionable steps to safeguard your systems.
Introduction:
Have you ever thought whether your organization’s cybersecurity measures are working? With such rapid movement in the digital world, even the slightest of risk or control gaps may equate to major vulnerabilities This guide will help you whether you are a seasoned professional or new to the cybersecurity domain, guide you on how to effectively identify, assess, and remediate these gaps. Let’s get together and make your defenses stronger.

1. Understanding Cybersecurity Risks and Control Gaps
- Cybersecurity risks and control gaps are a big problem in the always changing digital world and affect any size of organization. The term cybersecurity risk is related to loss, damage or disruption of the organization’s asset, operation or reputation which could be result from malicious cyber threats such as malware, phishing or insider attack. On the other hand, control gaps are the vulnerability or weaknesses in an organization’s
- Thereof, these risk and gaps occur due to several factors: outdated software, staff not trained, lack of standard processes or RGs, among others. An example is that many organizations fail to keep their security protocols up to date with routine updates, making them vulnerable to be tampered with. Additionally, human error like a misconfiguration firewall or user that isn’t being monitored continues to be a leading cause of control gaps.
- The consequences generated by these shortcomings can be traumatic. But that’s just the beginning of the losses, legal penalties, and reputational harm. Research from industry average estimates shows that approximately 60% of small businesses will close within six months of a significant cyber attack. For these kind of firms, the long term damage from breaches can be amplified as they face regulatory scrutiny and loss in consumer trust.
- They begin to address cybersecurity risks and control gaps by understanding their root causes. To address this first problem, organizations must adopt a proactive attitude, which includes performing regular risk assessments, effective implementation of control frameworks (for instance, NIST Cybersecurity Framework, ISO 27001), and cultivating a cybersecurity culture. Closing these gaps helps businesses not only protect its assets, but also give it resilience against emerging threats.
- In a nutshell, cybersecurity risk and control gaps are dynamic: they change as technology evolves and as criminals become more inventive. Today’s interconnected systems have to be safe and safeguarded by staying vigilant and adaptive.

2. The Importance of Identifying Risk and Control Gaps:
- Impact of unaddressed gaps on data, reputation, and compliance.
- Key statistics on the financial cost of cyber incidents.
- Benefits of proactive risk management.
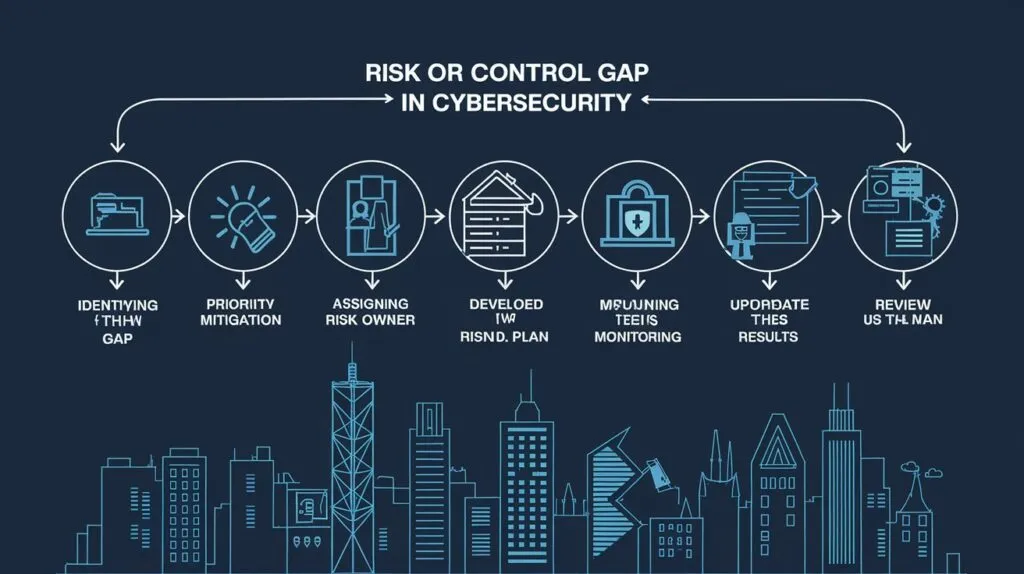
3. Steps to Identify Risk or Control Gaps:
- Conducting comprehensive risk assessments.
- Tools and frameworks for gap analysis (e.g., NIST, ISO 27001).
- Engaging internal and external stakeholders in assessments.

4. Developing an Action Plan to Address Gaps
- Determining order of gaps by risk spot and potential causing loss.
- Creating a roadmap with clear timelines and responsibilities.
- Allocating resources effectively to implement controls.
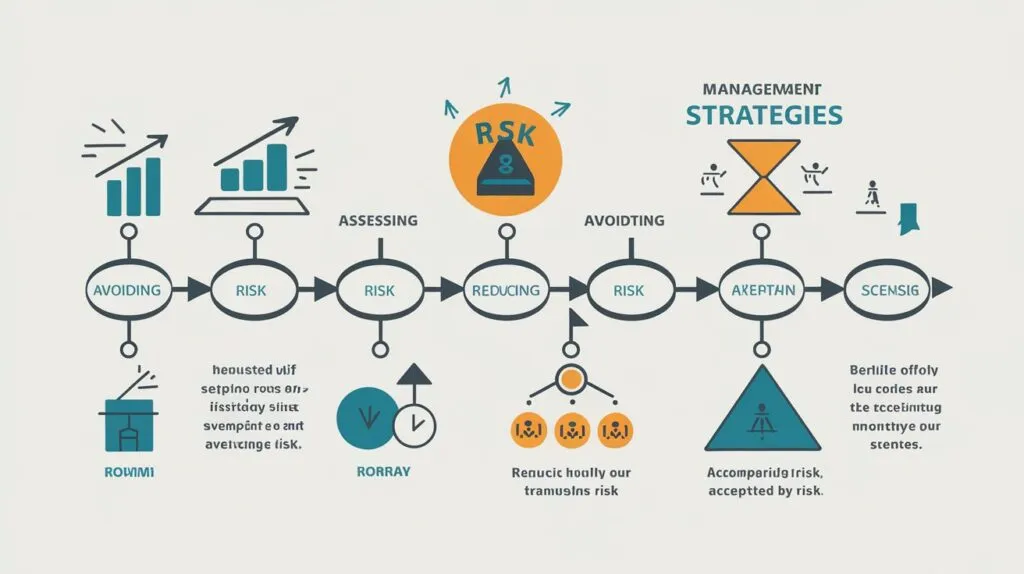
5. Implementing Controls to Mitigate Risks
- Types of controls: preventive, detective, and corrective measures.
- Examples of technical controls (firewalls, intrusion detection systems).
- Non-technical controls: policies, training, and vendor management.
6. Monitoring and Continuous Improvement
- Importance of regular audits and monitoring tools.
- Leveraging automation and AI to identify new vulnerabilities.
- Encouraging a culture of cybersecurity awareness.
7. Common Challenges and How to Overcome Them
- Resistance to change from stakeholders or employees.
- Budget constraints and resource limitations.
- Navigating complex regulatory landscapes.
8. Best Practices for Preventing Future Gaps
- Staying updated with the latest cybersecurity trends.
- Regular training programs for employees and IT staff.
- Establishing a feedback loop for continuous improvement.

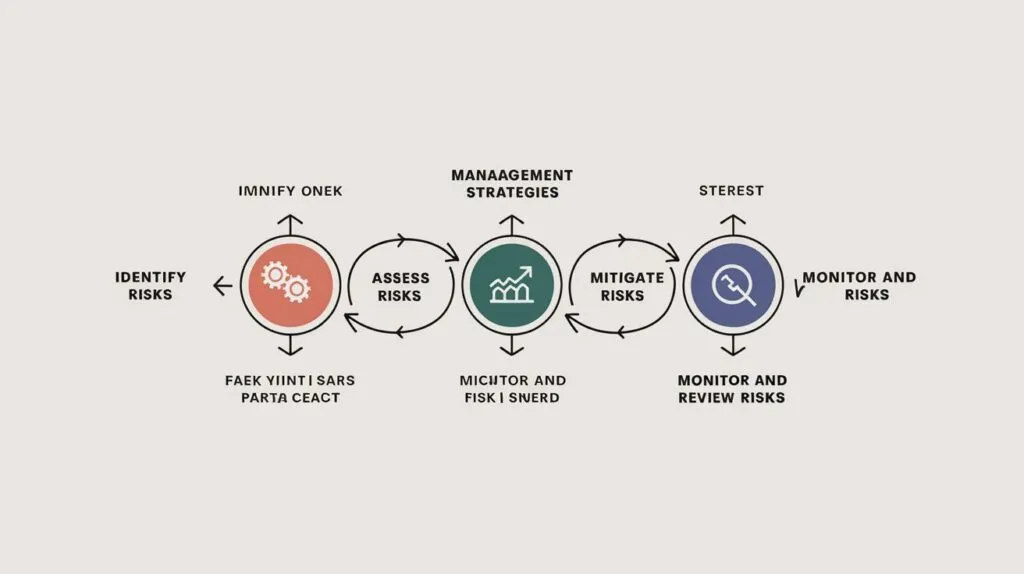
Risk Management Strategies
- Proactive risk management is vital for protecting your organization from potential threats while maintaining operational strength. By identifying, evaluating, and addressing risks, businesses can establish a robust defense against uncertainties across cybersecurity, finances, operations, and beyond.
- Start by conducting a detailed risk assessment to uncover vulnerabilities and rank them based on their potential impact. This prioritization ensures resources are directed toward the most critical areas. Strengthen defenses with preventive measures such as advanced firewalls, multi-factor authentication, and well-defined security policies to minimize exposure to risks.
- Equally important is fostering a culture of awareness and accountability. Educated employees are a critical line of defense, making regular training and knowledge sharing essential. Leveraging innovative tools and technologies, such as real-time monitoring systems and threat intelligence platforms, enables swift identification and resolution of emerging threats.
- To remain effective, risk management plans should evolve through regular reviews and updates, keeping pace with new challenges. Additionally, a strong business continuity plan ensures operations remain intact during unforeseen disruptions, providing a clear path to recovery.
- Implementing these strategies enhances organizational resilience, instills stakeholder confidence, and positions your business to thrive in a dynamic environment.
Conclusion:
From a strategic imperative standpoint, closing cybersecurity gaps isn’t a technical challenge. Knowing the risks you expose yourself to, knowing which tools to use, and creating a culture of security, will help you build resilient defenses against cyber threats. Every step you take today further fortifies your organization for tomorrow. Without any ado, start implementing these strategies and if you need specialized mentoring – cyber security professional sure!