Description:
Ready to learn everything about application security in 2025! Learn key strategies, best practices and tools for securing your software from cyber threats and delivering a safe user experience.
Introduction:
Application security is not merely a buzz word, which is today’s normal, it’s a must. It’s becoming increasingly clear that cyberattacks can be pretty advanced, and with that in mind, organizations need to focus on protecting their software from vulnerabilities that can put sensitive data at risk.
Did you know that of all cyber attacks, 43% are focused on application attacks? Compliance is just a part of protecting your software, and it’s critical as a way to build trust with your users and stay competitive. In this guide we will go over some basics of application security, including the types of threats, and how you can implement robust defenses. This article has everything you need to know regardless of whether you’re a developer, a security professional, or a business leader.
What is Application Security?
Application Security refers to the process of identifying, fixing, and preventing vulnerabilities in applications to ensure they remain secure from cyber threats. It encompasses a broad range of practices, tools, and techniques designed to safeguard applications from unauthorized access, data breaches, and other malicious activities throughout their lifecycle—from development to deployment and maintenance.
Key Components of Application Security:
- Proactive Security Measures: Strategies like secure coding and vulnerability scanning during development.
- Defensive Mechanisms: Firewalls, encryption, and access controls to protect against threats in real-time.
- Ongoing Monitoring and Updates: Regular testing, patching, and updates to mitigate emerging risks.
Types of Application Security Measures
- Authentication Controls:
- Verifies the identity of users (e.g., passwords, two-factor authentication).
- Authorization Mechanisms:
- Ensures users access only the resources they are permitted to use.
- Data Encryption:
- protects data in transit and at rest to stop unwanted access.
- Input Validation:
- Prevents malicious inputs like SQL injection and cross-site scripting (XSS).
- Vulnerability Management:
- Regular scanning and patching of application vulnerabilities.
- Firewalls and Web Application Firewalls (WAFs):
- Filters traffic to protect against common web-based attacks.
- Runtime Application Self-Protection (RASP):
- Real-time protection by monitoring and blocking attacks during execution.
Common Threats to Application Security
- Injection attacks (e.g., SQL Injection, Command Injection).
- Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
- Insider threats and human errors.
- Zero-day vulnerabilities and why they’re dangerous.
Best Practices for Application Security
- Code reviews and automated vulnerability scanning tools.
- How encryption helps safeguard data both in transit and at rest.
- Regular penetration testing and security audits.
Tools for Application Security
- A summary of the widely used security tools RASP, DAST, and SAST.
- Benefits of using security frameworks like OWASP.
- Features to look for in application security solutions.
DevSecOps: Integrating Security into DevOps
- How development and security teams may work together more effectively thanks to DevSecOps.
- Key tools and practices for DevSecOps adoption.
- Metrics to measure the effectiveness of DevSecOps implementation.
The Role of Compliance in Application Security
- Key regulations affecting application security (e.g., GDPR, CCPA, HIPAA).
- How to align application security with compliance requirements.
- Consequences of failing to meet compliance standards.
Application Security Trends for 2025 and Beyond
- AI and machine learning are becoming more common in security products.
- Evolution of cloud-native application security strategies.
- How quantum computing might change encryption and security.
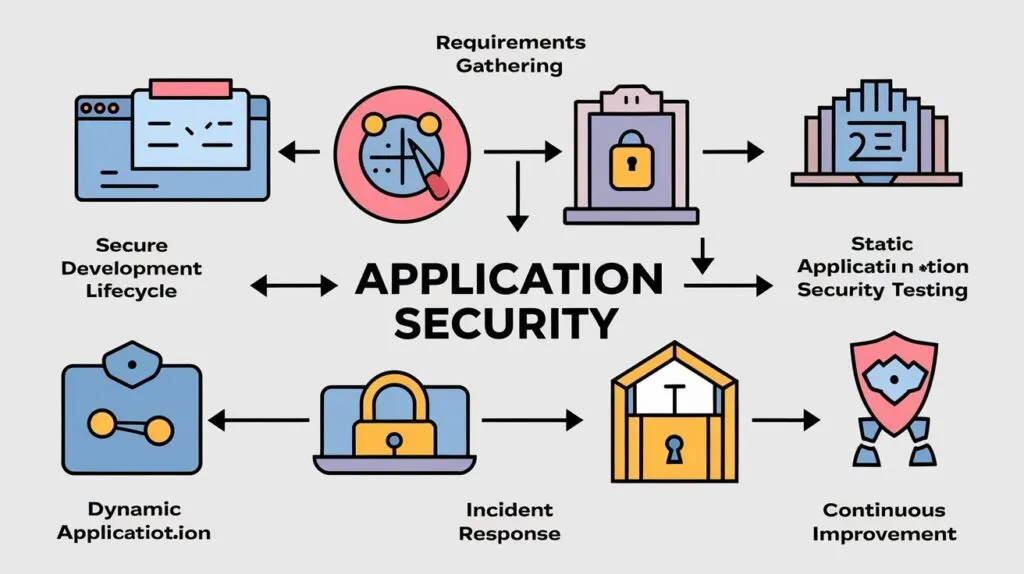
Flow Chart for Types of Application Security Measures
- A textual depiction of the flow chart can be seen below:
- Application Security Measures
├── Authentication
│ ├── Password Policies
│ ├── Two-Factor Authentication
│ └── Biometric Authentication
├── Authorization
│ ├── Role-Based Access Control (RBAC)
│ ├── Permission Management
│ └── Session Management
├── Encryption
│ ├── Data at Rest
│ └── Data in Transit
├── Input Validation
│ ├── Sanitizing User Inputs
│ └── Regular Expressions for Validation
├── Vulnerability Management
│ ├── Static Application Security Testing (SAST)
│ ├── Dynamic Application Security Testing (DAST)
│ └── Regular Patching
├── Web Application Firewalls (WAFs)
│ ├── Protecting Against DDoS
│ └── Blocking Malicious Traffic
└── Runtime Application Self-Protection (RASP)
├── Monitoring Real-Time Activity
└── Blocking Threats Dynamically

Conclusion:
In a world of ever changing cyber threats, application security is paramount. Whether it’s basic understanding, adopting of advanced tools and strategies, this guide covers everything about securing your software and protecting your users. By embracing these practices, it’s not about defending your applications, but about building out resilience and building trust in a world that is becoming evermore connected. Take the next step today: in order to evaluate where exactly you are, try to invest in modern solutions, and ensure that your organization has a culture of awareness surrounding security.


