what is cybersecurity program?
In today’s fast-changing digital world, cybersecurity is a big deal for everyone. A strong cybersecurity program keeps data safe, fights off cyber threats, and keeps digital systems sound. We’ll explore what a cybersecurity program is and the flow charts that help it work.
A cybersecurity program is a detailed plan that includes rules, steps, and tech to fight cyber attacks. It facilitates organizations keep up with security threats. This way, they can keep their digital stuff safe and sound.
Flow charts are key in cybersecurity. They help show and document security plans, how to handle incidents, and make decisions. There are many types, like linear and circular, each with its own job. They make complex security ideas easy to follow and act on.
Key Takeaways:
Cybersecurity programs are important to maintain digital assets and win the battle against cyber threats .Flow charts are a must for documenting, as well as showing security plans and steps.
• Linear and circular flow charts are different each with its own job in security .The use of flow charts well can help make a cybersecurity program more effective .The first step towards a strong security plan is knowing about the cybersecurity programs and flow charts .ow charts are a crucial tool for documenting and showing security plans and steps.
• There are different flow charts, like linear and circular, each with its own role in security.
• Using flow charts well can make a cybersecurity program more effective.
• Knowing about cybersecurity programs and flow charts is the first step to a solid security plan .
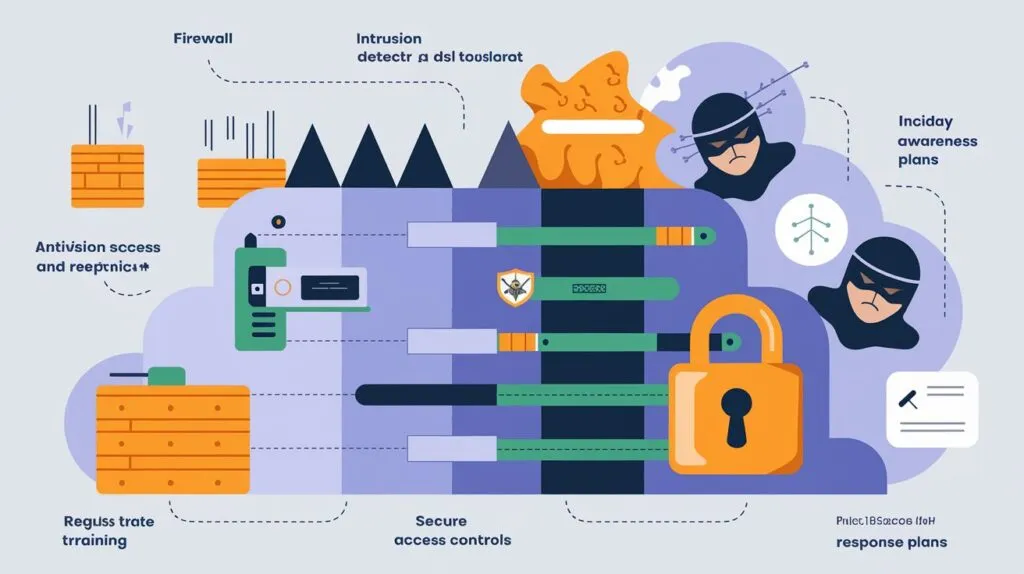
Understanding the Fundamentals of Cybersecurity Programs
Cybersecurity programs are key to protecting our digital world. They have three main parts: security infrastructure, cybersecurity objectives, and digital protection basics. Knowing these is vital for strong security.
Core Components of Security Infrastructure
Firewalls, intrusion detection, access controls, encryption are all part of a good security setup. They come together to combat cyber threats. They ensure safety of the data and systems.
Key Objectives and Goals
The main goals of cybersecurity programs are to avoid asset destruction, running business, and comply with rules. They bring strong security, check the risk, and watch out threats. It helps keeping everything safe.
Building Blocks of Digital Protection
Strong cybersecurity starts with basics like strong passwords, secure networks, and updates. These steps help protect against cyber attacks. They make a strong defense against threats.
“Cybersecurity is not just a matter of tech, it’s truly a people, process, and a proactive way of thinking issue.”
Knowing about cybersecurity’s parts, goals, and basics helps protect digital assets. It keeps organizations safe from new cyber threats.
The Evolution of Cybersecurity Program Development
Time has drastically changed the world of cybersecurity. This change is thanks to new technology and the shifting threat landscape. We’ve moved from simple computer systems to today’s connected digital world. The history of cybersecurity is filled with growth and adjusting to new challenges.
At first, cybersecurity focused on basic protection like antivirus and firewalls. But as security program advancements came along, these efforts grew. Now, they include things like checking for vulnerabilities, planning for incidents, and managing risks.
1. The internet and more digital devices have made it easier for attacks “You should define cybersecurity not in tech space, it is truly [a people] process space first.”
2. New tech like cloud computing, mobile devices, and IoT has made things harder. Security experts must keep updating their plans.
3. Threats like APTs, ransomware, and attacks from countries have made cybersecurity programs more important. They need to be proactive and strong.
As the cybersecurity history keeps moving, companies must stay alert and quick to respond. By keeping up with security program advancements, they can protect their data and systems better.
To stay one step ahead of the adversaries, we have no alternative to constantly adapting and innovating our defenses, with the only way to win the cybersecurity battle.
Essential Elements of a Robust Cybersecurity Program
Building a strong cybersecurity program needs careful planning. It involves a detailed risk assessment, solid security policies, and effective incident response plans. Each part is vital for protecting digital assets.
Risk Assessment Frameworks
Identifying and fixing risks is crucial for any cybersecurity plan. Frameworks like NIST, ISO, or FAIR are helpful. They help organizations assess risks and decide how to act.
Security Policy Development
Security policies form the foundation of a good cybersecurity program. They outline the organization’s goals, how to use digital tools, and roles. This ensures everyone follows the same cybersecurity elements.
Incident Response Planning
Even with strong prevention, being ready for security issues is key. Incident response planning is essential for handling cybersecurity breaches. It includes identifying threats, knowing roles, and communication during an incident.
| Key Cybersecurity Program Elements | Description |
| Risk Assessment | Systematic evaluation of potential threats, vulnerabilities, and their impact |
| Security Policies | Guidelines and procedures to protect digital assets and ensure compliance |
| Incident Response | Plans and techniques for identifying, containing, and recovering from security incidents |
“A robust cybersecurity program is not a one-time effort, but a continuous process of adaptation and improvement.”
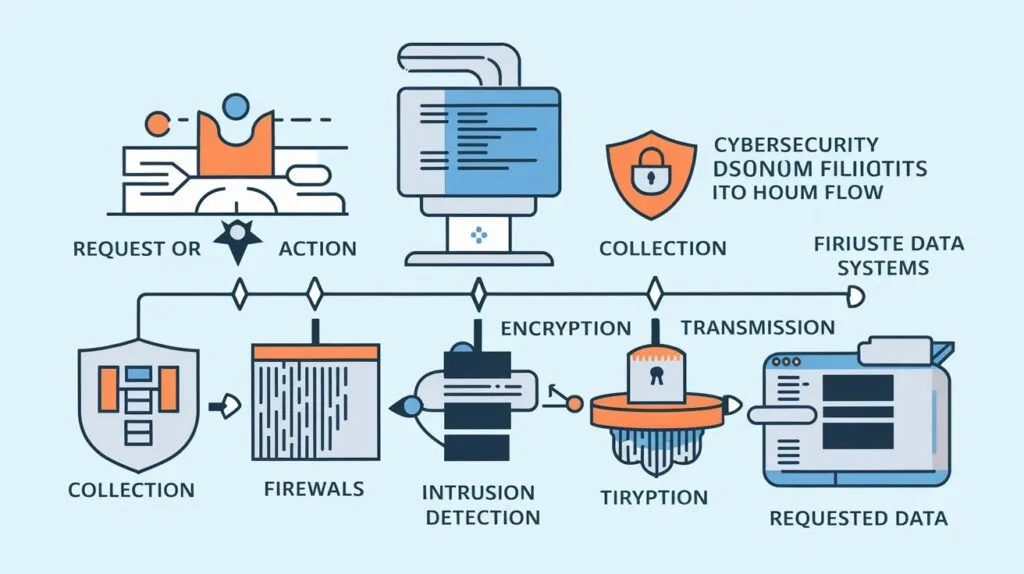
Flow Chart Types in Security Documentation
In cybersecurity, flow charts are essential for showing how security processes work. They help document and use digital protection plans. These security flow charts are crucial for safeguarding digital information.
Flow charts are great for simplifying complex security information. They help everyone understand the security setup and data flow. This is true for network diagrams and incident response plans.
Types of Security Flow Charts
- Process Flow Charts: Show the steps and choices in a security process.
- System Architecture Diagrams: Show how security parts work together, like hardware and software.
- Risk Assessment Frameworks: Explain how to find, study, and fix security risks.
- Incident Response Workflows: Tell who does what in case of a security problem.
These visual security representations make security plans clear. They help teams work together and make good decisions.
| Flow Chart Type | Purpose | Key Benefits |
| Process Flow Charts | Illustrate the step-by-step sequence of actions and decision points within a specific security process. | Promotes understanding of complex security procedures, identifies bottlenecks, and facilitates process optimization. |
| System Architecture Diagrams | Depict the interconnected components of the security infrastructure, including hardware, software, and communication channels. | Enhances visibility into the security ecosystem, facilitates troubleshooting, and supports informed decision-making regarding infrastructure changes. |
| Risk Assessment Frameworks | Showcase the methodologies used to identify, analyze, and mitigate potential security risks. | Provides a structured approach to risk management, enables the prioritization of security efforts, and supports compliance with industry standards. |
| Incident Response Workflows | Outline the actions and responsibilities of various teams and stakeholders in the event of a security breach or incident. | Ensures a coordinated and efficient response to security incidents, minimizes the impact on business operations, and facilitates post-incident analysis and improvement. |
Using security flow charts helps organizations document and use their cybersecurity plans. This makes their security stronger and more resilient.
Linear vs. Circular Flow Charts in Security Protocols
Security professionals often use two main flow chart models: linear and circular. Each has its own benefits, making them perfect for different parts of a cybersecurity program.
Benefits of Linear Flow Charts
Linear flow charts are simple and follow a step-by-step process. They are great for showing how to handle incidents, assess risks, and follow other security steps. Their clear, logical order makes them easy for teams to follow and use, especially for standard procedures.
Advantages of Circular Flow Models
Circular flow charts are more dynamic and show the ongoing nature of security work. They highlight the feedback loops and cycles that keep a cybersecurity program strong. These charts are best for showing how to manage risks, respond to incidents, and keep monitoring security.
Hybrid Approaches
Some groups choose a hybrid security model that mixes both linear and circular flow charts. This mix uses the clear steps of linear charts and the ongoing nature of circular ones. It lets teams adjust their documentation to fit their unique cybersecurity needs.
The right choice between linear, circular, or hybrid flow charts depends on an organization’s cybersecurity needs. Knowing the benefits of each helps security teams pick the best way to share and carry out their security plans.
Implementation Strategies for Security Flow Charts
Adding security flow charts to a company’s cybersecurity plan is key. These diagrams make security steps clear and easy to follow. This helps businesses protect their digital world better.
Here are some important steps for flow chart implementation:
1. Teach Employees: It’s vital to train staff on what security flow charts do. Offer detailed training to make sure everyone knows how to use them right.
2. Security protocol execution: These charts help security teams follow steps without mistakes. They show the right actions and decisions clearly.
3. Chart integration into current systems: It’s important to fit security flow charts into what your company already does. Keep them up-to-date and easy for everyone to see.
By following these steps, companies can use security flow charts to boost their cybersecurity program. This makes their digital world safer.
| Approach | Benefits |
| Comprehensive Staff Training | Ensures widespread understanding and adoption of security flow charts, empowering employees to leverage these tools effectively. |
| Seamless Integration with Existing Processes | Enhances the long-term relevance and impact of security flow charts, making them a vital component of the organization’s cybersecurity infrastructure. |
| Continuous Chart Maintenance and Updates | Keeps security flow charts current and responsive to evolving threats, ensuring their ongoing effectiveness in guiding security protocol execution. |
Best Practices for Program Documentation
Keeping your security documentation up to date is key to a strong cybersecurity program. Following best practices helps keep your security plans current, consistent, and easy for everyone to access.
Standard Operating Procedures
It helps to create thorough Standard Operating Procedures (SOPs).These SOPs guide you through tasks like handling incidents, managing vulnerabilities, and controlling access. Good SOPs make sure everyone does things the same way, lower the chance of mistakes, and make training new people easier.
Documentation Maintenance
Just making your security documents isn’t enough. They have to be accurate and current. Security experts should regularly review and update these documents. This includes feedback from users and changes in security rules and practices.
Version Control Systems
Using version control systems is a smart move. Tools like Git or SVN help track changes and let you go back to older versions if needed. They also help teams work together on security documents. This way, everyone has the latest information.
| Best Practice | Description | Key Benefits |
| Standard Operating Procedures (SOPs) | Detailed step-by-step instructions for security-related tasks | Promotes consistency, reduces errors, enables efficient training |
| Documentation Maintenance | Regular review and update of security documentation | Ensures accuracy and relevance in changing security landscape |
| Version Control Systems | Tools for tracking changes, reverting, and collaborative development | Maintains documentation integrity and provides access to latest information |
A good cybersecurity program has security documentation as its cornerstone. It deletes inconsistency, encourages cohesion and facilitates perpetual improvement.”
Common Challenges in Program Management
Dealing with cybersecurity can be tough. Security experts face many challenges that slow down their work. One big issue is how fast cyber threats change. This means teams must always be ready to update their security plans to keep up.
Also, the tech world is getting more complex. Security teams have to work together across many systems and apps to protect everything. Money and resources are often tight, making it hard to invest in strong security.
Lastly, keeping up with changing rules and standards is a big challenge. Security pros need to be quick and smart to meet these new requirements. This helps keep their security systems strong and up-to-date.
FAQ
What is a cybersecurity program and what are the different types of flow charts used in security documentation?
A cybersecurity program protects an organization’s digital assets from cyber threats. Flow charts help show security protocols and plans. They come in types like linear, circular, and hybrid.
What constitutes a security infrastructure’s essential elements?
Firewalls, antivirus, intrusion detection systems, etc. belong to a security infrastructure. It also features security monitoring tools, encryption, and access controls. These work together to defend against cyber attacks.
What are the key objectives and goals of a cybersecurity program?
The main goals of a cybersecurity program are to protect data and ensure business continuity. It also aims to meet regulatory requirements and reduce cyber risks. This is done through security controls, threat monitoring, and incident response planning.
What are the building blocks of digital protection in a cybersecurity program?
The foundation of digital protection includes asset management and vulnerability assessment. It also involves risk analysis, security policy development, and employee training. Continuous monitoring and improvement are also key.
How has the development of cybersecurity programs evolved over time?
Cybersecurity programs have grown from basic network security to a holistic, risk-based approach. The cornerstone of a good cybersecurity program is security documentation.
What are the essential elements of a robust cybersecurity program?
A strong cybersecurity program has risk assessment frameworks and comprehensive security policies. It also includes incident response planning, employee training, and continuous improvement. These elements defend against various cyber threats.
What are the best practices for maintaining cybersecurity program documentation?
For maintaining cybersecurity program documentation, create standard operating procedures and update them regularly. Use version control systems to ensure accuracy. Ongoing maintenance is vital for a program’s success.
What are some common challenges faced in managing a cybersecurity program?
Challenges in managing a cybersecurity program include keeping up with threats and securing funding. It also involves maintaining staff expertise and ensuring integration with existing systems. Proactive planning and continuous improvement help overcome these challenges.