Description
Do you want to produce powerful infographics about information security in 2025? Are you looking for some design trends, essential design components, and advice to assist you become more aware of cybersecurity?
Introduction
You ready for stepping up your cybersecurity messaging? When you are in a world of visual communication where infosec information graphic is your secret weapon for learning and engagement. Infographics can simplify complex security protocols and a well crafted infographic can draw attention to hot new threats. In this guide, we’ll discuss why infographics are a must have for the cybersecurity space, discover what makes them work and provide tips on how to design them to ensure they leave a lasting impression. So we say let’s take information security from understood to unforgettable!
Why Use Infographics for Information Security?
• The power of visual learning: to why visuals help with message retention.
• Simple examples of complex cybersecurity concepts in visuals.
• The way infographics can help increase awareness and engagement with different audience . Mples of complex cybersecurity concepts made simple through visuals.
• How infographics boost awareness and engagement across different audiences.
Key Elements of an Effective Information Security Infographic
• Data-driven storytelling: Showing using statistics to emphasize important points.
• Simplicity in design: Persuading readers enjoy technical jargon.
• Visual hierarchy: More or less helping the audience wade thru the narrative with ease.
• Clear call-to-action: Encouraging in two ways; one in promoting proactive cybersecurity measures.
Popular Themes for Information Security Infographics
• What type of cyber threats are, for example phishing, malware, and ransomware.
• Personal and corporate cybersecurity best practices.
• Cybersecurity trends of 2024.alware, ransomware).
• Best practices for personal and corporate cybersecurity.
• Emerging trends in cybersecurity for 2024.
• The cost of cyberattacks: This does economic and reputational damage.
Design Tips for Engaging and Effective Infographics
• Selecting the ideal color scheme: striking a balance between readability and aesthetics.
• Font selection: So you can ensure clarity and professionalism.
• Iconography and graphics: Improving on understanding with symbols.
• Canva to Adobe Illustrator selection: Ensuring clarity and professionalism.
• Iconography and graphics: Using symbols to enhance understanding.
• Professional infographic-making tools, such as Adobe Illustrator and Canva.
How to Distribute and Maximize the Impact of Your Infographic
• Broad reach through sharing on social media platform (LinkedIn, Twitter, etc.)
• Add infographics to cybersecurity reports and presentations.
• Targeted awareness via leveraging email campaigns.
• Placing infographics on websites and blogs for better SEO purposes) for broader reach.
• Including infographics in cybersecurity reports and presentations.
• Leveraging email campaigns for targeted awareness.
• Embedding infographics on websites and blogs to improve SEO.
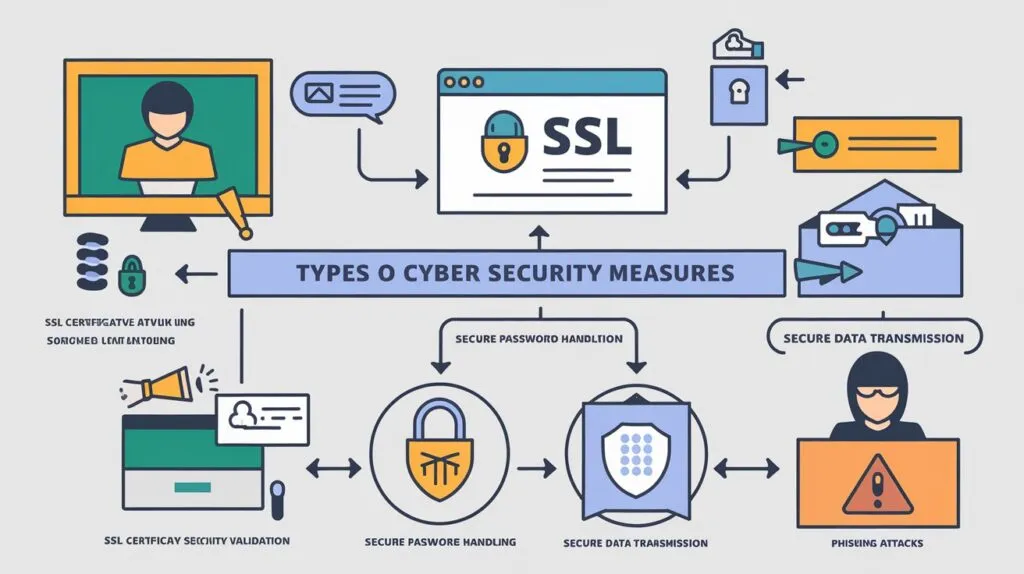
Flowchart Structure
1. Introduction (Top Node)
- Node Title: “What is Information Security?”
- Content: Information security and why it is so important in protecting data against cyber threats.
- Arrow Down →
2. Core Components of Information Security (Branch Node)
Split into three branches to highlight the key pillars:
- Branch 1:Confidentiality
- Ensuring data is accessed only by authorized individuals.
- Branch 2:Integrity
- Maintaining accuracy and reliability of data.
- Branch 3:Availability
- Guaranteeing data is accessible when needed.
Arrows Merge Down →
3. Types of Cyber Threats (Main Node)
• Phishing: to use phony emails to collect private information.
• Ransomware: Types of malware that locks up files unless a ransom is paid.
• Malware is software that is intended to interfere with and harm systems.
• Social Engineering: Causing people to give confidential information by manipulation.
Arrow Down →
4. Best Practices for Staying Secure (Branch Node)
Branches to provide actionable advice:
• Branch 1: Combine using strong passwords and multi factor authentication.
• Branch 2: Increase the rate of patching software and systems.
• Branch 3: Help employees know how to recognise threats.
• Branch 4: Back data up regularly, and encrypt them.
Arrow Down →
5. Emerging Trends (Main Node)
- A Threat Detection Threat threat can be detected artificially.
- Increased cloud security focuss in cybersecurity: o Artificial intelligence in threat detection.
- Zero-trust architecture.
- Increased focus on cloud security.
Arrow Down →
6. Call to Action (Bottom Node)
- Node Title: “Take Action Now!”
- Content: Encourage users to:
• Go to a website/resource for more information.tices.
o Visit a website/resource for more information.
Conclusion
As well as being visually appealing, infographics are a powerful tool for conveying vital Communications in the world of cyber security. With integrating fascinating data, impactful design and handy flow, you can transform your message into a lever for action. Discover how to become good in creating impactful information security infographics, and keep your audience not just informed but expecting to help protect their digital world with them!


